Understanding Information, Cyber and Network Security
Taylor James, Network Architect
In mid-September of 2022, Uber, one of the largest companies in the world, discovered it had been hacked after the hacker announced in the company’s internal communications system, “I am a hacker and Uber has suffered a data breach.”
In June of last year, Michigan-based Flagstar Bank notified customers of a data breach where hackers stole the social security numbers of 1.5 million customers. While the attack itself happened in December 2021, Flagstar didn’t discover the breach until much later.

Data breaches have been increasing for years, and even those that thought they were being diligent are not immune. Medibank Private Ltd, the largest health insurance provider in Australia, disclosed data pertaining to almost all of its 4 million customer-base had been accessed by an unauthorized party. Their stock price slid 14%, the biggest one-day dip since the company was listed.
When choosing the best information security plan for your business, it’s best to understand some key terms – how they’re related, and where they’re different.
The Pillars of Cybersecurity: C.I.A.
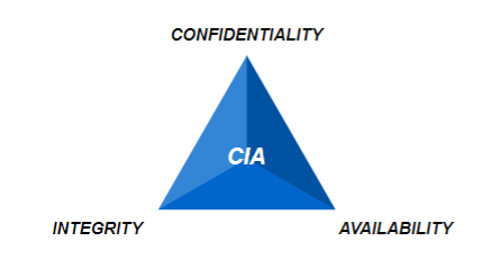
When beginning your cybersecurity journey and assessing cyber risk, keep in mind the following foundations. An issue with one or more of these are as could contribute to a cybersecurity incident.
- Confidentiality – private, sensitive and proprietary information is only accessed by those that are authorized to do so.
- Integrity – data, files and software is not changed or altered and is authentic.
- Availability – data and systems need to be available to other systems, users and institutions to complete tasks.
Cybersecurity
Cybersecurity protects against external and internal threats and defends your digital data that lives on your network, as well as individual devices that connect to that network. Cyber-attacks often try to access or change data, as well as extort money from companies or individual users by holding data ransom and interrupting normal business operations.
Why you Need Protection
Cybercrime is unpredictable. Incidents like those above show how threats and data breaches are becoming increasingly common for companies big and small as society relies more and more on the digital space. It is absolutely critical in today’s environment that companies protect sensitive information from unauthorized access – both their own as well as their customers’ – to preserve trust and credibility.
Information Security and Data Governance
Information Security encompasses the controls and policies used to protect information from unauthorized access and data leaks – whether done maliciously or unintentionally. This includes Personally Identifiable information (PII), customer account details, financial data or even intellectual property. There are countless strategies to do this in the physical world, but the digital space is a whole new playing field where the potential threats are often unseen.
Data Governance is the custodial practice of securing data. Enforcing least privilege access based on an employee’s role and secure storage of data are a few examples. Knowing what kind of data you currently house and where it’s stored is the first step to Information Security.
Network Security
Network security it is a set of rules, parameters and configurations intended to protect the integrity, confidentiality and accessibility of computer networks and data using a combination of hardware technologies and software. The network perimeter is no longer confined to the main office – telework and remote work are now a norm for most of today’s businesses and network security needs to keep pace with this change. Entec regularly consults with clients on designing the best network security strategies available – including segmentation, managed firewalls, secure remote access and real time network monitoring.
Do You Have a Cybersecurity Plan?
Most cyber-attacks are crimes of opportunities – exploiting the weakest systems with the least of amount of effort is an enticement for a cybercriminal. Trust and credibility are critical for consumers and companies when choosing where to spend their hard-earned dollar or who to partner with in their next business venture. That’s why it’s more important than ever to stay protected.
The saying “if you don’t have a plan, plan to fail” rings true. Having the proper Incident Response, Information Security Policies, vulnerability risk management and disaster recovery are critical to navigating today’s cybersecurity threats.
At Entec, we work with clients to evaluate their cybersecurity strengths and weakness. Beyond anti-virus protection, we can provide vulnerability assessments to identify threats so they can shored up before an intrusion happens. We also help implement intrusion detection and prevention systems so the proper parties are alerted and can respond to cybersecurity events in real time.
